Try-hack-me
Agent Sudo : Walkthrough
Agent Sudo is an Easy room on Tryhackme created by Deskel. This machine requires enumeration, hash cracking, steganography, and Privilege Escalation.
Alright the room has a total of 5 tasks, or 4 if you just want to count the actual tasks. Task 1 has a note from the room author DesKel to have fun!
Deploy the machine, wait a few minutes for it to boot and we will dive right in.
Enumerate
Everyone has got to be familiar with the first step after getting a machine IP by now, I hope?
We do some port scanning and recon using our favorite tool Nmap
#nmap -sS -sV -A -T4 -vv <target ip>
We get a html page that tells us that agents should use their own codename as user-agent to access the site.
We see an announcement for the Agents from Agent R. The tryhackme hint was to change the “User-agent” with “C”. So we started Burpsuite to intercept the request.
After capturing the request we modified the “User-agent” with “C” and forward the request.
We got an Agent Name and from the message, we know that the password of the Agent is weak so now we can Bruteforce FTP with Hydra.
#hydra -l chris -P /usr/share/wordlists/rockyou.txt <target IP> ftp
Now we know the password for the Agent we can log in through FTP.
#ftp <target IP>
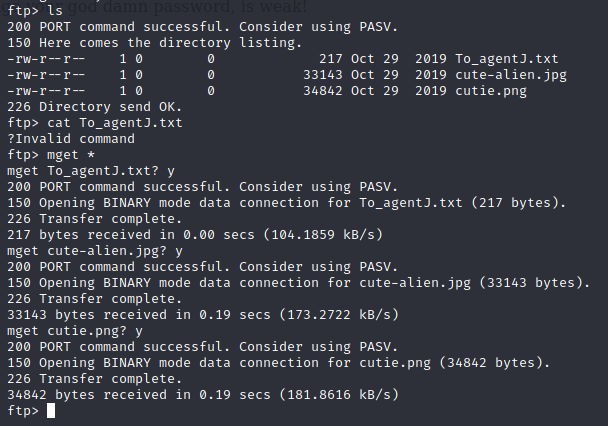
We have successfully logged in through FTP and we checked for the content and we got images and a text file, we downloaded all the files using “get command”.
#ls
#mget *
By viewing the “To_agentJ.txt” file the message was login password for the chris is stored in the fake picture.
The questions at this point consist of a zip file, which we do not have. We also need a steg password. Could it be that a zip file is hidden in one of the files we downloaded? We run binwalk on the png file which is the most likely to contain some hidden files.
#binwalk cutie.png -e
So we used “zip2john” to crack the zip file for password with this command
#zip2john 8702.zip > Output.txt
and then we used john to crack the hash.
#sudo john Output.txt
And we got the password alien, so we tried to extract the zip file but unzip command didn’t work so we used this command:
#7z x 8702.zip
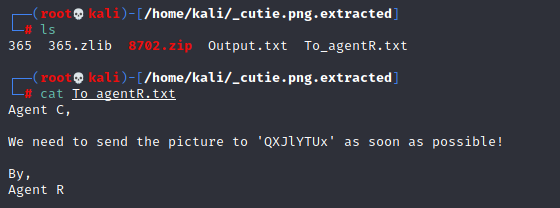
After entering the password and extracting the zip file we got this message.
#cat To_agentR.txt
This message was from Agent R we decoded this ‘QXJlYTUx’ message using Cyberchef. Cyberchef suggests auto decoding.
We got the password Now only images file left is “cute-alien.jpg” so we used the “steghide” tool to retrieve hidden info.
#steghide --extract -sf cute-alien .jpg
The info got extracted to “message.txt” after viewing the message we got username and password.
Now we log in through SSH into the machine using the username and password we found now we can read the user flag
#ssh james@<target IP>
Privilege Esclation
We checked for the permission the user has with “#sudo -l” command.
#sudo -V(To check the version)
check the exploit on exploit DB where we can find the CVE number as well.
Using the exploit we found, we can indeed spawn a root shell and get our root flag in /root directory.
That's the end of this writeup, I hope you learnt something from this and had some fun too😀.
Thank you very much for reading. I hope you find this blog useful.
!!!!Happy Hacking!!!!




















Comments
Post a Comment