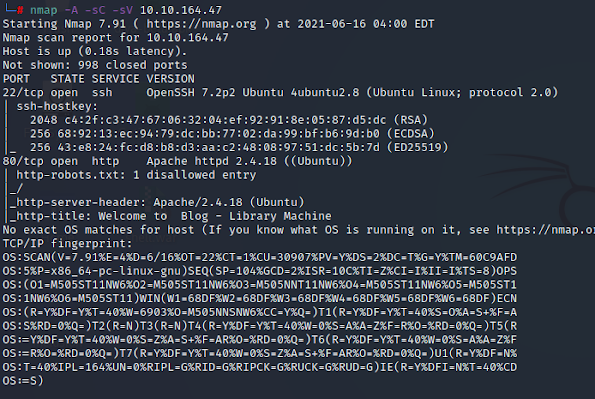
Try-hack-me Agent Sudo : Walkthrough Agent Sudo is an Easy room on Tryhackme created by Deskel. This machine requires enumeration, hash cracking, steganography, and Privilege Escalation. Alright the room has a total of 5 tasks, or 4 if you just want to count the actual tasks. Task 1 has a note from the room author DesKel to have fun! Deploy the machine, wait a few minutes for it to boot and we will dive right in. Enumerate Everyone has got to be familiar with the first step after getting a machine IP by now, I hope? We do some port scanning and recon using our favorite tool Nmap #nmap -sS -sV -A -T4 -vv <target ip> Looks like we have some open ports running on the machine. A web server is running on port 80. Let's open it and investigate further. We get a html page that tells us that agents should use their own codename as user-agent to access the site. We see an announcement for the Agents from Agent R. The tryhackme hint was to change the “User-agent” with “C”. So we sta...