Try-hack-me
Lian_Yu : Walkthrough
This post is a walkthrough of an Arrowverse themed beginner CTF box on Tryhackme.
Let’s get started by deploying the machine. Now, after deploying the machine, start with a basic Nmap scan and see which ports and services are open and running on the particular IP address.
#nmap -A -sC -sV <target IP>
Port 80 is open and running so let’s look at the webpage first..
The First step is to check the page source and robots.txt but no information found there, so let’s move to enumeration.#gobuster dir -u http://<target IP>/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
Looks like we have found a directory /island let’s look at it.
The webpage looks like this at first instance but when I saw the source code I realized the the code word is also given in as vigilante but is in the white text.
So here we got our code word. I then ran gobuster again with the addition of the new directory I had found directory inside island directory as /2100.
#gobuster dir -u http://<targetIP>/island/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
Now let’s check /island/2100
There is nothing relevant on the page here so let’s check the source code maybe we will find something interesting there.
It is telling something about .ticket it might be a hidden directory or a .ticket extension, I then ran gobuster once more, but this time, I ran with an extension:#gobuster dir -u <http://<targetIP>/island/2100> -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .ticket

Going to http://<target IP>/island/2100/green_arrow.ticket we’ll see this
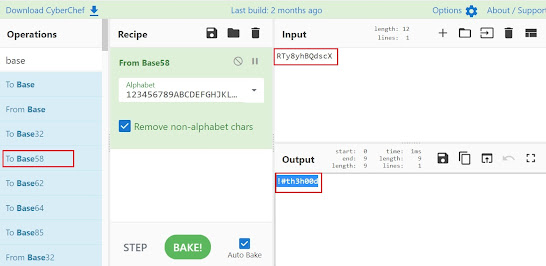
The text in the picture is a password of some sort, lets use CyberChef to decode it. After analyzing a bit I got to know it was a base58 cipher.
So now we have another interesting string !#th3h00d. Remember that ports 21 and 22 are open. Maybe vigilante and !#th3h00d are the credentials.
It doesn’t work on SSH but it worked on FTP.
#ftp <target IP>
Here I can see 4 files I need to get: The 2 PNGs, the one JPG, and the last file was the “.other_user” file. I downloaded all of them using “#mget *”. This should download all the files to your local directory.
Reading the “.other user”, I came across this:
Here I can see various names, which could be potential usernames and/or passwords. One main name was “Slade” which was used the most .
But then I moved on to analyze the images that I downloaded on my local machine. The first image, Leave_me_alone.png looks corrupted.
I then searched for file signatures on google:
From the results, I copied the hex code for the png file as shown below:
Next, hexeditor was used to change the hex code to open the file:
#hexeditor Leave_me_alone.png
Post making changes to the file and saving it the file was fixed and gave output as:
Now we have a password but it does not look like the ssh one as I tried using it there. We have another image named aa.jpg. So we will try to extract information with Steghide with the password mentioned.
#steghide --extract -sf aa.jpg
#ls
#unzip ss.zip
#ls
Steghide revealed two files passwd.txt and shado, viewing both the files.
And through Shado file we can see the password as M3tahuman.
I then entered the username, Slade, with password M3tahuman on the ssh and got into the box.
#ssh slade@<target IP>
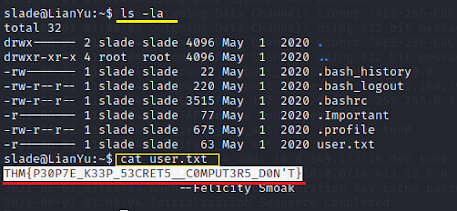
Once I got into the box I simply did #ls -la command to find the user.txt flag and #cat users.txt to grab and submit on Tryhackme.I then had to upgrade my privileges to root. To do this I ran #sudo -l. This command lets you know what commands our user can do as the root user. #sudo -u root /usr/bin/pkexec /bin/bash
And Final step,
#ls
#cat root.txt
Thank you very much for reading. I hope you find this blog useful.

























Comments
Post a Comment